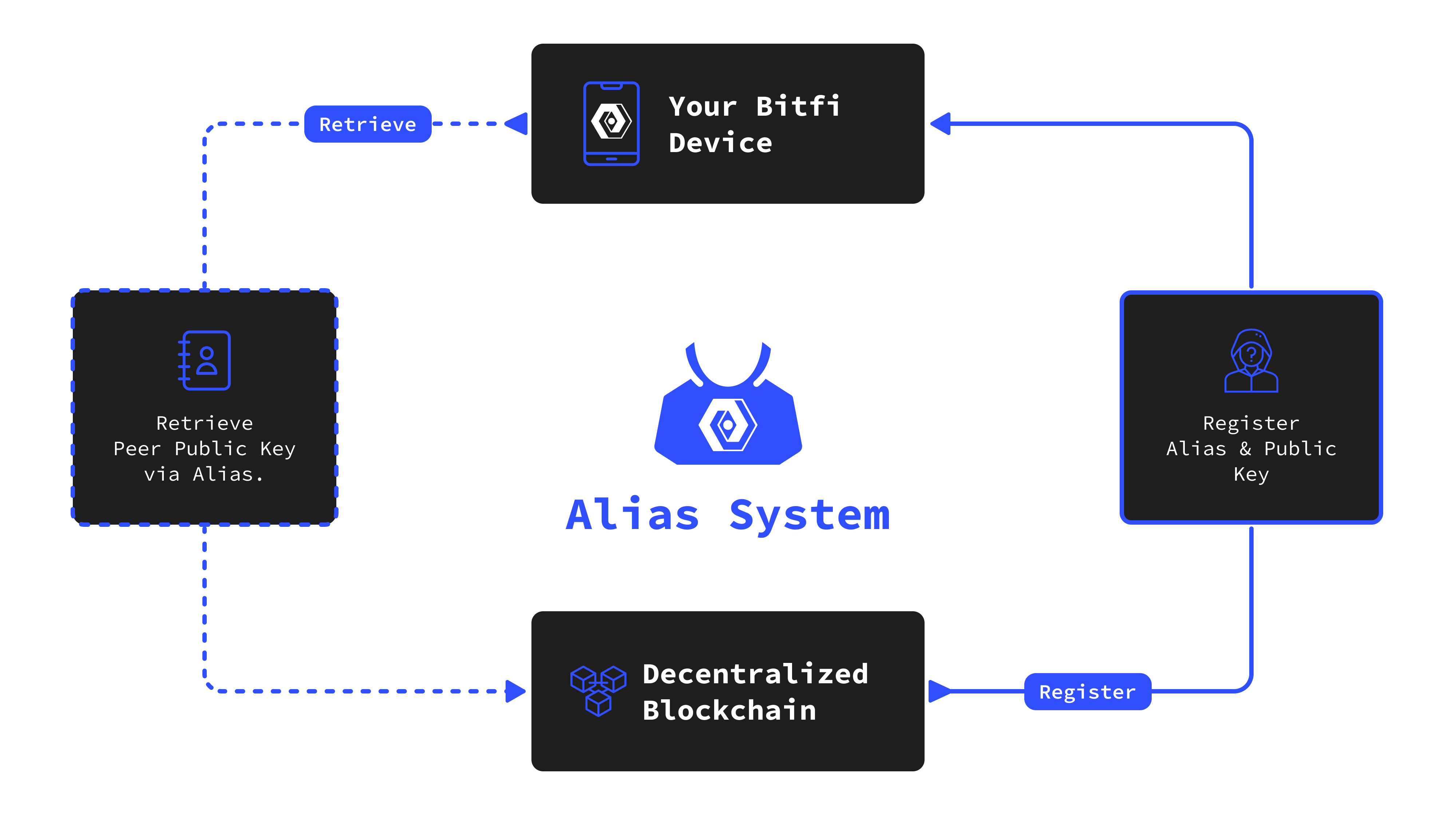
The Bitfi Peer-to-Peer Phone System represents a significant advancement in secure communication technology, combining state-of-the-art cryptography, blockchain integration, and hardware security to meet the demanding requirements of intelligence agencies, governments, military branches, and defense contractors.
By addressing every layer of potential vulnerability—from user authentication and device integrity to communication channels and data handling—Bitfi provides a comprehensive solution that stands resilient against current and emerging threats.