How It Works
1. Secure Access
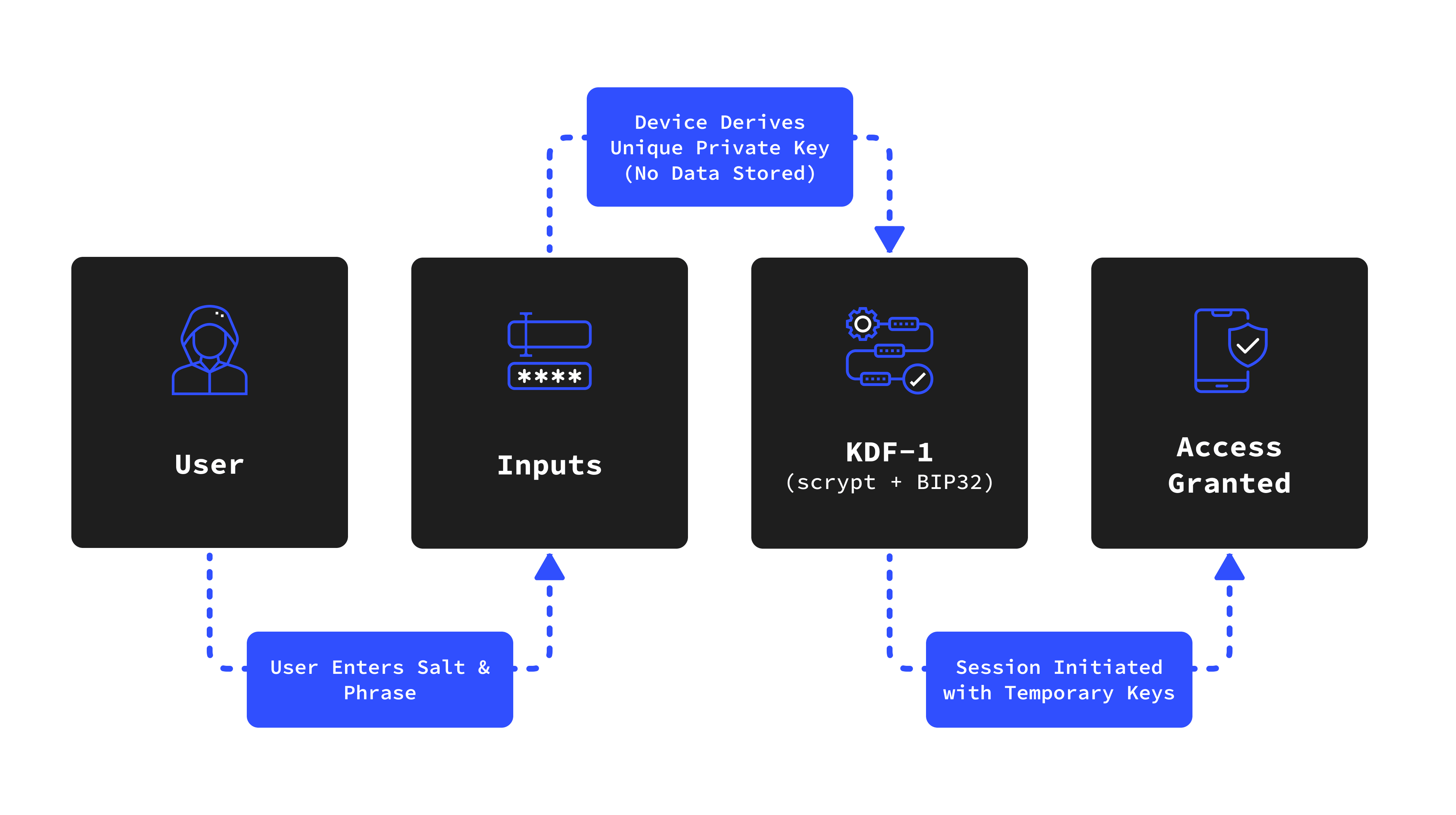
Salt & Phrase Authentication: Your unique Salt & Phrase combination is your key to access. Memorized by you, stored nowhere else.
Stateless Operation: Since the device stores no data, there’s no need for passwords. Authentication is secure and immediate.
2. Establishing a Connection
Alias System: Register a unique alias on a decentralized blockchain. No phone numbers—just secure, untraceable identities.
Private Key Verification: Only devices with embedded private keys can connect to the Bitfi network, ensuring all participants are authenticated.
3. Direct Peer-to-Peer Encryption
Independent Encryption Initialization: Both caller and recipient devices independently randomize encryption keys for each call, which are never reused.
KDF-1, KDF-2, KDF-3: Advanced key derivation functions ensure robust, unique keys for every session.
4. Secure Communication
MEDIA.async360 & APP.async360: Proprietary applications handle voice and text with top-tier encryption methods.
Bitmap Text Rendering: Text messages are converted into bitmap images in real-time, leaving no text data in memory.
5. Session Termination
Instant Data Purge: Ending a session triggers an immediate wipe and overwrite of all data.
Device Reversion: Post-session, the device is indistinguishable from a brand-new unit—no residual data, no traces, nothing to exploit.
Salt & Phrase Authentication Workflow